What is Ransomware?
Ransomware is a type of malicious software that locks you out or encrypts your files, and then makes a demand that you pay a ransom, in order to get a decryption key that will give you back access to your files.
According to the Federal Bureau of Investigation (FBI), on average, 4,000 ransomware incidents occur every day, and the annual cost is $1 billion. This includes ransoms paid to cybercriminals, plus the money and time spent in recovering from these attacks.
Talk to our cloud security experts to know about our ransomware protection
What is the difference between malware and ransomware?
Malware and ransomware are not the same even though the words are often used interchangeably.
Malware is a short form for “malicious software” which is a broad term used to describe all forms of malicious software.
Some popular examples of malware are:
- Trojan horse.
- Adware.
- Ransomware.
- Virus.
- Spambots.
- Spyware.
From the examples above, you can see that ransomware, is only a form of malware. This is to say that all ransomware is malware, but not all malware is ransomware.
History of ransomware
Ransomware attacks are not new. Businesses, governments, and even individuals have been victims of ransomware attacks for over three decades now.
Ransomware attacks became popular in the mid-2000s. However, the first recorded case of a ransomware attack took place sometime in 1989 when a PC Cyborg was launched by an evolutionary biologist, Dr. Joseph Popp.
His method of infection was very basic. He stored the virus on disks said to contain sensitization programs on AIDS and sent the floppy disks to his victims. The Trojan encrypted files got activated on the victims' computers as soon as they tried to play the disks.
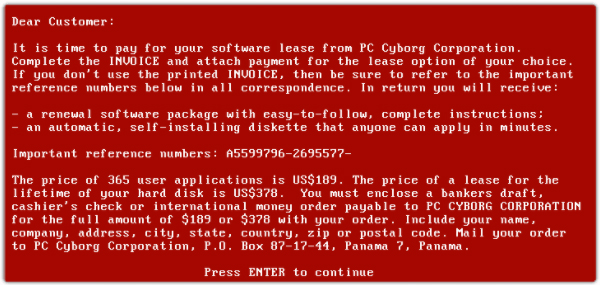
Then, a message popped up on their screens, demanding a ransom of $189 to get their files unlocked.
So many things have changed since that first ransomware attack of 1989 especially in terms of sophistication and reach. The methods of dissemination, especially, have changed. The amount lost by organizations and individuals has also skyrocketed in the past few years. According to the National Security Institute,the average amount of money requested as a ransom fee rose to $200,000 in 2020 from $5,000 in 2018.
How do ransomware attacks happen?
Ransomware attacks have been on the increase recently mainly because it is considered by cybercriminals to be very lucrative. They can launch an attack easily, and compared to what they can make from it while expending minimal efforts, the margins look good, as many organizations would rather pay the ransom than put a halt to their business processes.
Depending on the ransomware strain involved, a ransomware attack usually follows two steps.
Encryption of data
Ransomware mostly uses data encryption software to encrypt the data in a system it infiltrates. The encrypted data then becomes useless to the user without a specific decryption key which can only be given by the attacker after a ransom is paid.
Ransom demand
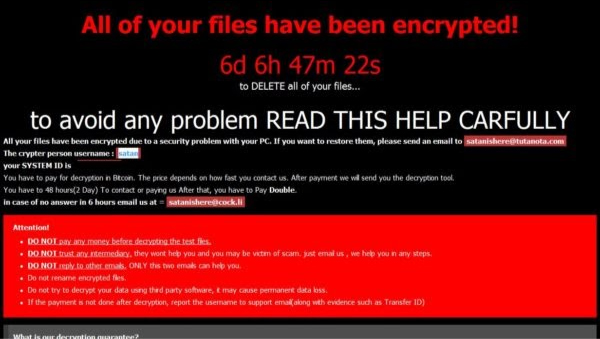
Soon after the victim's files get encrypted, a message pops up on their screen demanding that they pay a ransom to get back access to their files. The message would also contain instructions like how much ransom to pay, how to make the payment, and the deadline.
How does ransomware infect your system?
There are many variants of ransomware, but they are mostly delivered through three common vectors.
- 1. Email phishing
- 2. Remote desktop protocol (RDP)
- 3. Malvertising
1. Email phishing
Email phishing is the most common vector for propagating ransomware. These emails come with malicious links, attachments, or both.
The way it works most times is that an unsuspecting user gets an email from someone they know which contains a malicious attachment like a fake receipt or a fake order form. These attachments are executable files that look like Microsoft Office files, or PDFs. If the user clicks on the attachment, the ransomware infiltrates and gets automatically downloaded into their system.
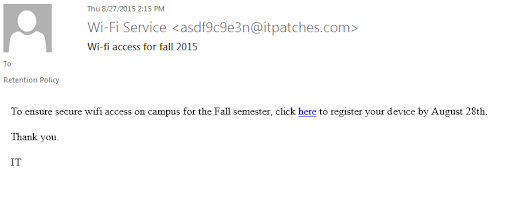
In a similar fashion, the user can get an email with a link. When they click on the link, they will be asked to fill in their credentials. If they do, the credentials get stolen and can be used to gain entrance and install the ransomware.
2. Remote Desktop Protocol (RDP)
In 2020 alone, enterprise networks experienced a total of 3.3 billion RDP brute-force attacks. And according to Cyware,1.4 million RDP brute force attacks were attempted every day by April 2020.
An RDP is a Windows system protocol that is designed to give IT support access to control another system remotely in order to fix an issue. Unfortunately, this is the second most popular ransomware attack vector as RDP ports are easily compromised.
RDP security is based on having a strong password protocol, and many users ignore this protocol. This makes it easy for hackers to penetrate vulnerable RDP ports, and harvest their credentials.
As soon as they succeed, they can then go past endpoint protection and begin to either wipe out data or encrypt them.
3. Malvertising
In this form of attack, malware is distributed by injecting malicious codes into online adverts and served to consumers through legitimate ad networks.
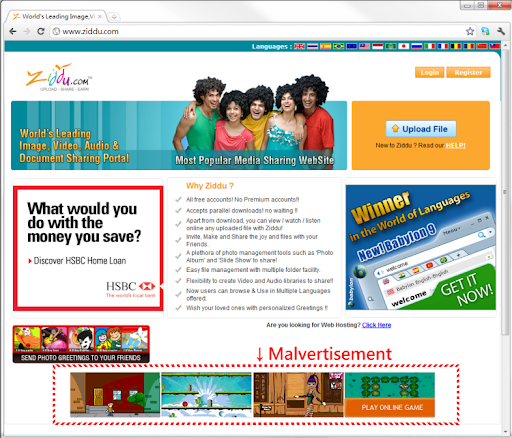
If a user clicks on these ads, the corrupted code injected in the advert will install malware on their computer, or they can get redirected to a malicious website for an advanced attack.
Unfortunately, malvertising attacks can happen whether the user clicks on the links or not.
The most common form of malvertising takes place when the user clicks on the link, as clicking on the malicious link makes the attack more effective.
Four main things can happen when a user mistakenly clicks on the link
- 1. The user is redirected to a malicious website different from the one in the ad.
- 2. A javascript code that will install malware on the user's system is executed.
- 3. Redirecting the user to a malicious website that looks like the real site but is operated by the hacker.
- Execution of an exploit kit - a malware designed to scan the system and exploit the weaknesses in it.
However, although less common, there are instances when the user doesn't click on the malicious link and they still get a malvertising attack. The most common occurrence is the drive-by download.
Drive-by download
In this case, the malware takes advantage of the vulnerabilities in your browser to secretly download and install the malware on your system even though you are merely viewing the ad without taking any action. This mostly occurs if your browsers and apps are outdated.
What are the different forms of ransomware?
There used to be two different forms of ransomware: Crypto ransomware and Locker ransomware. But over the years, ransomware tactics have evolved.
Currently, ransomware comes in five main forms.
1. Crypto ransomware
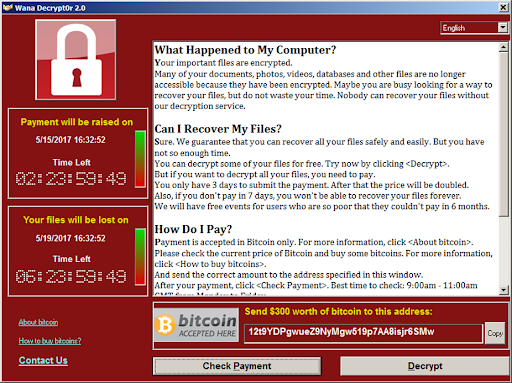
This is the most common form of ransomware. It makes use of complex algorithms to lock all or some of the data on the victim's system which cannot be unlocked without a decryption key. And the key can only be obtained after a ransom has been paid.
2. Locker ransomware
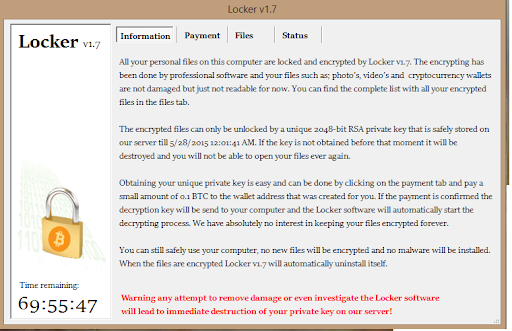
This is the second most common form of ransomware. Here, a user is blocked from logging in or having access to their files using non-encrypting malware. Payment is demanded from the user to regain access to their files.
3. Scareware
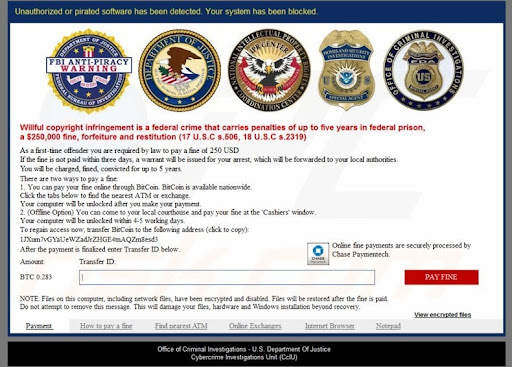
This form of ransomware uses scare tactics to compel the victim to pay the ransom. Just like in the locker ransomware, the victim's files don't get damaged. Instead, they get pop-ups with an official-looking seal like that of the FBI or the Department of Justice, telling them that they have broken a law and to avoid punishment, they should pay a fine.
4. Leakware
This form of malware threatens to expose sensitive personal or company files to the public unless a ransom is paid. This usually leads to extortion because even if the victim pays the ransom, the attacker could demand more payment as they still have access to the files.
5. Ransomware as a Service (RaaS)
This form of malware is hosted by a pro hacker and offered on a pay-for-use basis. The hacker hosts and offers the ransomware to criminals on the dark web as a subscription using the SaaS business model. After execution, a part of the loot is paid to the hacker based on their agreed-upon terms.
What causes ransomware attacks?
Ransomware attacks happen randomly sometimes, other times, they are targeted. But most times, one, or a combination of these five things is always behind a ransomware attack.
1. Phishing emails
This is the most common cause of ransomware attacks. In fact, an analysis carried out by Fortinet reported that 1 in every 3,000 emails contains malware including ransomware.
Hackers trick users into clicking a link or opening an attachment containing a malicious file. These files usually look like PDF, Word documents, or ZIP files. Once the user clicks on it, it activates a script that downloads and executes the malware that either locks their systems or encrypts their files.
2. Little or no knowledge about cybersecurity
To infiltrate and attack a system, all a hacker needs is one staff who has little or no cybersecurity knowledge. When the staff in an organization don't have the necessary cybersecurity training, it makes the whole organization vulnerable to ransomware attacks.
3. Poor security practices
This is an offshoot of the last point. Many times, if a user has little cybersecurity knowledge, they are prone to engage in poor security practices. If they have weak passwords, for instance, it becomes easy for any malicious actor to gain access to their system and infiltrate the organization's network.
4. Poor update management
A lot of ransomware attacks occur due to software vulnerabilities. Every device has updates and patches that are regularly released to prevent them from getting exploited. If you have a poor habit of updating and patching your devices and apps regularly, they could easily get breached.
5. Open RDP access
An RDP's security is dependent on how strong the password protocol is, and many times, users ignore these protocols. This creates an opportunity for malicious actors to attempt to exploit it for their own use.
With the use of an open-source password-cracking tool, cybercriminals can try to brute-force the RDP password so they can log in as administrators. If they succeed, they gain full control of the system and activate the ransomware encryption program.
Want a secure cloud now with no ransomware fear
How does ransomware affect businesses?
Generally, ransomware affects businesses in two major ways:
1. Loss of money
When a ransomware attack occurs, the victim is always asked to pay a ransom to regain access to their files or to get them decrypted.
2. Disruption of business activities
Moreso, because of the attack, most of the business operations may have to be halted until the system is recovered and restored.
These two things impact an organization in the long run, and we are going to discuss that in detail subsequently.
World-famous ransomware attacks
Below are five of the most popular ransomware attacks that took place in 2021.
1. CNA Financial
On the 23rd of March 2021, CNA Financial, one of the largest insurance firms in the US fell victim to “a sophisticated cybersecurity attack”.
The hacker group known as Evil Corp used the Phoenix Locker ransomware to encrypt 15,000 devices and a lot more computers used by their remote workers. CNA Financial had to pay $40 million as ransom to get back their data and restore their system.
2. JBS Foods
In May 2021, JBS Foods, one of the biggest meat processing companies in the world, got hit by ransomware and had to stop operations at five of its largest plants in the US. The attack was executed by REvil, a popular and sophisticated Russia-based hacking group.
It was confirmed on the 10th of June that JBS paid the hackers $11 million ransom in Bitcoin to stop the disruption and contain the impact on their supply chain.
3. Colonial Pipeline
Colonial Pipeline, the largest “refined products” pipeline in America went offline on May 7, 2021, when a hacking group, Darkside infiltrated the company's internal business network and billing system. This resulted in a widespread shortage of gas in a lot of states, as Colonial Pipeline transports more than 100 million gallons of fuel every day.
The company had to pay a ransom of $4.4 million to the group. Thankfully, the Department of Justice announced, on June 7, 2021, that it had recovered $2.3 million out of the ransom.
This ransomware attack could be said to be the most popular attack in 2021 because it resulted in a lot of chaos and panic due to the disruption of gas supplies along the East Coast of the US.
4. Kaseya
The same hacker group behind the attack on JBS Foods, REvil, made headlines on July 2, 2021, after an attack on Kaseya, a firm that provides IT solutions for major companies worldwide. This attack ended up affecting about 1,000 other organizations in multiple countries as the hackers infiltrated both Kaseya's direct clients and their customers.
REvil demanded a $70 million ransom to be paid in bitcoin. However, Kaseya refused to pay, choosing instead to work with the FBI.
A few weeks later, the FBI was able to access Kaseya's servers and got the encryption keys, and in the end, no ransom was paid.
5. Brenntag
Brenntag, a German chemical distributor, got attacked by the same notorious hacker group behind the Colonial Pipeline attack, Darkside. The attack took place on April 28, 2021. The hackers stole 150GB of their data and threatened to leak it if the ransom of $7.5 million wasn't paid.
Brenntag ended up paying $4.4 million in ransom on May 11 after negotiating with the criminals, which is still one of the highest ransoms paid in history.
Popular ransomware variants in 2020-2021
With more people working from home between 2020 and 2021, it is not surprising that the number of ransomware attacks has been on the rise.
In fact, 2021 can be said to be the worst year ever in the history of ransomware attacks. According to this mid-year report, 2021 had a 93% increase in the frequency of cyberattacks when compared to 2020. And between January and June alone, 304.7 million ransomware attempts were recorded.
Many variants of ransomware have emerged in the past few years. Here is a list of seven of the most popular ransomware variants that were recorded between 2020 and 2021.
1. REvil
Also known as Sodinokibi, this ransomware variant was discovered in April 2019 and operates via the ransom-as-a-service (RaaS) model. It is notorious for encrypting victims' files at an alarming rate and doubling the ransom if it is not paid within the stipulated time.
It became very famous after it attacked JBS Foods, one of the biggest meatpacking enterprises in the world, in June 2021.
2. Ryuk Ransomware
Ryuk ransomware, just like REvil, also operates using the ransomware-as-a-service model. It was discovered in August 2018, and is considered the most common ransomware variant.
The ransomware targets government agencies and large enterprises and compromises victims' systems using a malware Trojan known as TrickBot.
It is popular for its private affiliate program. Towards the end of 2020, its affiliates attacked an average of 20 companies every week, including a massive wave of attacks targeted on the US healthcare system. And they were also behind more than 90 million out of the 304.7 million recorded ransomware attempts in the first half of 2021.
3. DarkSide ransomware
DarkSide ransomware was discovered in August 2020, and in its first nine months of operation, more than $90 million ransom payments in Bitcoin were made by its victims.
This ransomware variant was responsible for shutting down the largest fuel pipeline in the United States - the Colonial Pipeline and caused the gasoline shortage that took place in gas stations on the U.S east coast in 2021.
It equally operates on the ransomware-as-a-service (RaaS) model and is notorious for encrypting and exfiltrating victims' data from the servers.
Their ransom demands range from $200,000 to $2 million.
4. Cerber Ransomware
Just like the previously mentioned ransomware, Cerber also runs on the ransomware-as-a-service model. This ransomware reportedly attempted a total of 52.5 million malware attacks in the first six months of 2021.
5. Zeppelin ransomware
This ransomware variant was discovered in November 2019 by GrujaRS, and equally operates as ransomware-as-a-service. It is a variant of the Buran ransomware, and its targets are healthcare and technology companies in the U.S and Europe.
6. Snake ransomware
Also known as the Ekans ransomware (Snake spelled backward), the snake ransomware variant was discovered in January 2020 and makes up six percent of all ransomware attacks today.
Operationally, Ekans is selective about its victims as it mainly targets industrial control systems. If it succeeds, it stops virtual machines, harvests the administrators' credentials, and encrypts all the files on their network.
And instead of following a uniform extension, the Snake ransomware modifies file extensions using a hexadecimal, five-random character string, evading detection in the process.
7. Maze ransomware
Maze was discovered in 2019 and became popular for publishing sensitive data of some victims in the healthcare sector. They launch attacks and infect their victims' systems using exploit tools like Fallout and Spelvo.
Maze is considered one of the most notorious ransomware strains, encrypting and exfiltrating data, and threatening to publish the information in the data if the ransom isn't paid.
Thankfully, they announced they were going to stop their operations in October 2020, but by then, they were responsible for 12 percent of all the ransomware attacks in Europe and North America.
How do you prevent ransomware attacks?
The most effective way you can prevent a ransomware attack is by combining the use of technology and cybersecurity training. Here are a few tips to help you.
1. Engage and train end-users
Since the targets are end-users, make it a duty to engage with and train your employees on the threat that ransomware poses and how it operates. Show them how to identify malicious emails.
For instance, you can organize phishing simulations to teach them how best to recognize and deal with phishing emails. Continually educating your employees will help them understand how to prevent and avoid potential ransomware attacks.
2. Double-check every link before clicking Online User Guide
When it comes to ransomware, you can never be too careful. Phishing emails is one of the most common ways ransomware attacks occur, and you should never click on any link that looks suspicious as a simple click can deploy ransomware into your system.
This precaution also applies to email attachments. Verify email addresses and confirm the sender before opening any attachment. Do a double-check to ensure that the attachment you are about to click on is not a JavaScript or an executable (.exe) file. If you are not sure of a file or a link, forward them to IT support for sandbox tests.
3. Scan your emails
You can never be too careful. Moreover, it is possible to slip up on a bad day. So make sure you scan all incoming emails and authenticate them using the Domain Message Authentication Reporting and Conformance technology. Enable very strong spam filters to detect phishing emails. Filter all executable files and prevent them from getting to end-users.
4. Install ad blockers
No matter how careful you are, there is ransomware that can be deployed to your system through malvertising and drive-by downloads even when you don't click any link. The best way you can prevent this from happening is by installing ad blockers on your browser.
5. Use VPN whenever you are using public Wi-fi
Public Wi-fi is usually porous and not secure. Whenever you want to use public wi-fi, make sure you use a VPN. That way, even if an attacker performs a man-in-the-middle attack, your system will be protected.
6. Implement the principle of least privilege (POLP)
The principle of least privilege is a zero-trust principle. In other words, no user should have administrative access unless it is absolutely necessary. Instead, grant users the minimum access they need to perform their tasks successfully. That way, nobody will tamper with sensitive files mistakenly.
7. Update your software regularly
As simple as this sounds, it is the most basic preventive measure against ransomware attacks. No software or program is perfect. They always need to be updated and patched. Make use of a patch management tool to automatically deploy patching for your computers, networks, software, and operating systems whenever they are available. This will keep them safe from vulnerabilities.
8. Make use of anti-virus and anti-malware programs
Use robust cybersecurity apps to block malware so they won't even come near you. Some antivirus apps can block unsafe links, unsafe websites, and sketchy downloads. You can equally install whitelisting software to prevent the execution of unauthorized applications. Set these programs to conduct regular scans on your systems.
9. Disable Macro scripts
When you get Microsoft Office files as email attachments, consider making use of Office Viewer software to view the files instead of macro scripts.
10. Back up your data regularly
Many times, once a ransomware attack occurs, it is extremely hard or in some cases, impossible to decrypt the encrypted files successfully. Provide an offline backup to store your files and lock them. If it is possible, encrypt and isolate these back-ups so as to keep them safe from network breaches.
What is the possible impact of ransomware?
Below are five ways ransomware attacks could impact an organization.
1. Financial losses as a direct result of the attack
Although not reported, many organizations cave in and pay the ransom demanded. This usually runs in hundreds of thousands and millions of dollars for big organizations.
For instance, when Colonial Pipeline was attacked in May 2021, the organization had to pay a $4.4 million ransom to the hackers.
2. Disruption of regular operations
Ransomware attacks affect the productivity of a business negatively. All revenue-generating operations are usually put on hold following an attack until the system is secured and the company regains access to its files.
A good example is JBS Foods. On the 31st of May 2021, the company got hit by an organized cybersecurity attack. Due to the attack, JBS had to temporarily shut down its beef operations in the United States. They had to halt operations in some of their meat processing plants, and it wasn't until the 3rd of June before they could fully restore global operations.
3. Loss of revenue
This is a direct result of the previous point. When the business process is ground to a halt, the company is bound to lose money for as long as it lasts. Judging from available reports, 66% of businesses attacked by ransomware experienced a significant loss in revenue.
4. Loss of C-Level talent
Many companies have been reported to lay off staff, especially C-level employees, after such attacks because of the losses they incurred. And in some terrible cases, the organization had to shut down operations completely.
5. Potential harm to an organization's reputation
Many times, when organizations get hit by ransomware, it affects their reputation.
According to this research, 64% of those that responded said they felt their employers reputation suffered after the attack. Even though they are victims, most organizations choose to keep ransomware attacks a secret and only tell their partners and sometimes, customers, because of the stigma attached to it.
Who are the targets of ransomware?
Ransomware targets are generally classified into two groups.
1. Spray-and-pray targets
This group represents the majority of ransomware attacks. Here, ransomware infections are disseminated through random vectors to unsuspecting victims. Most times, the actors acquire a list of emails or compromised websites and direct attacks at them indiscriminately.
2. Big-time player targets
This second group, however, is specifically targeted, and a lot of research is done before they get targeted. They are usually big organizations with high-value assets. Organizations that cannot afford to have downtime, and can pay a high ransom. A typical example is the JBS case mentioned above.
Most times, big-time player targets are organizations that:
- Can comfortably pay the ransom.
- Have loopholes in their cybersecurity infrastructure.
- Have a pain point that the hackers can squeeze to make them pay the ransom.
Hackers usually have five types of organizations that they consider as prime targets. They are:
1. Healthcare
Since the Covid-19 pandemic of 2020, the health industry has become a top target for ransomware attacks.
It is estimated that 45 percent of ransomware attacks are targeted at healthcare organizations. In 2020 alone, 560 healthcare facilities were affected by ransomware attacks, according to a report by Emisoft.
Hospitals, medical clinics, testing centers, and other healthcare organizations can't afford to have downtime or have their systems locked. They need to always have access to electronic medical records to keep administering and monitoring patients, especially Covid-19 cases.
This makes them more likely to pay a ransom, and as such, top ransomware targets.
2. Education
A report by BlueVoyant revealed that universities had a 100 percent increase in ransomware attacks between 2019 and 2020. And not just universities, colleges, public district schools, and trade schools are all ransomware targets as the student data they store is very sensitive, and they would not want to have their classes disrupted either.
3. Banking, Financial Services, and Insurance (BFSI)
This sector is also a prime target because it is where the money is. Banks experienced a 520% increase in ransomware attempts and phishing emails between March and June of 2020 alone, and 90% of all financial institutions were ransomware targets in 2017.
Many times, the ransomware attacks in the financial sector do not result in encrypted data, but the stealing of sensitive data. The victims are then threatened to pay the ransom or risk having their data published online.
4. Manufacturing and Industry
Attackers usually target manufacturers because most of them run factory operations round the clock and can't afford to have them disrupted. They would rather pay the ransom than allow disruptions that will affect the supply chain.
Industrial organizations with industrial control systems (ICS) that control physical equipment in their industrial operations are also prime targets. Hackers can hold their critical infrastructure hostage and pressure them into paying hefty ransoms easily.
5. Information Technology
The 2021 Ransomware Threat Report revealed that the IT sector experienced a 65% increase in ransomware attempts between 2019 and 2020. Because of Covid-19, many organizations were forced to employ remote work models which made it easier for attackers to explore gaps in their cybersecurity and locate vulnerabilities. Hackers usually deployed malicious emails to disarm victims in the IT sector to infiltrate their system and encrypt their data.
How to remove ransomware
How to remove ransomware As much as you take security measures, it is also important you know how to respond in case you get attacked.
In the case of a ransomware attack, take the steps below to remove the ransomware, limit your damages and reduce costs.
1. Isolate the infected computer
Identify the affected system and quarantine it immediately. Turn off all the machines that could have been potentially affected by the ransomware, isolate them, and disconnect them from your network. This way you can prevent the ransomware from spreading and infecting the network or shared drives.
It will also give you ample time to recover data, contain the damage, and prevent the condition from getting worse.
2. Contact law enforcement
As soon as you discover that you are a victim of a ransomware attack, notify the local law enforcement and any of the field offices of the U.S Secret Service or the Federal Bureau of Investigation (FBI) immediately, and ask them to assist you.
3. Secure backup data
Secure your backup systems at this point and take them offline. And make sure they are free of malware before you do so.
4. Identify the type of ransomware you are dealing with
The way you will respond to crypto-ransomware is different from the way you will respond to locker ransomware. So make sure you identify what you are dealing with.
5. Try to regain access and remove the malware
If the ransomware you are dealing with is the locker ransomware and not the crypto-ransomware, you can try and get rid of it and regain access to your system.
How to get rid of ransomware:
- Reboot your system in safe mode.
- Install anti-malware software in it.
- Scan the infected computer to locate the ransomware.
- Restore the system to a previous state.
If your IT department cannot handle this, however, get an expert to help you remove the malware from your system. Since your files are all backed-up, you may not need to bother decrypting them.
6. Identify the source of the security breach
Even if you decide to abandon the encrypted data, you will still have to deal with the infection and prevent it from spreading further. This means you need to identify how it happened in the first place and tighten that loose end to prevent a second occurrence.
This could mean changing all your online account passwords. It could also mean changing all system passwords as soon as the malware is removed.
7. Restore data
Since your system is already backed up, restore it to the most recent version. You can then decide to abandon the encrypted data. This way, there will be no need for you to pay any ransom.
Should you pay ransom to criminals?
If your system has been compromised, you'd probably be willing to pay the ransom especially if it is little compared to the potential losses you could incur. However, you must understand that the people you are dealing with are criminals and may just take your money and run.
It is not advisable to pay the ransom because there is no guarantee that the encrypted files will be decrypted. The criminals could even decide to keep extorting you.
Worse still, it is reported that 80% of victims that paid ransom demands got exposed to a second attack.
In an article on how to respond to ransomware attacks, the FBI had this to say“The FBI does not support paying a ransom in response to a ransomware attack. Paying a ransom doesn't guarantee you or your organization will get any data back. It also encourages perpetrators to target more victims and offers an incentive for others to get involved in this type of illegal activity.”
What will be the definite fix for ransomware in the future?
Presently, there is no permanent solution for ransomware attacks. The best you can do right now is to take proactive measures to protect your networks and ensure that you don't become a victim of an attack.
You must continuously educate your employees, for instance, to help them understand how ransomware works and how they can prevent an attack from succeeding.
In conclusion, you can no longer choose to be on the sidelines if you wish to be safe. You must take cybersecurity more seriously and invest in it as a matter of . You must always be vigilant and never take software updates for granted. If every organization begins to take cybersecurity more seriously, there will be a rapid decline in these attacks.
Want a cloud with enterprise backup in place
Frequently Asked Questions
How is ransomware detected?
It is immediately detected as soon as you login to your system mostly via a flash message, demanding the ransomware with contact details to get in touch with the hacker. The information may also include a list of warning messages by the same hacker if you try to oversmart them.
Who are ransomware hackers?
Ransomware hackers are the cybercriminals mostly from lawless territories. They keep on trying to login to the secure systems or by finding loopholes in weaker security protocols to access and take over the control of the systems.
Can ransomware spread through Wi-Fi?
It depends upon the nature of the attack. Yes, some of the ransomwares have the potential to penetrate through Wi-Fi and spread across your network adversely impacting all the connected resources. Though some ransomware attacks are just confined to the system they break into.
What to do if you're a victim of ransomware?
The very first action should be the immediate disconnection from the internet. You can then follow the steps given on the section (Heading of that section) in the above article.
What happens if you get Ransomware?
Once you get the ransomware, the files on that particular system will be encrypted using secret decryption code. You get a notification from the hackers and steps to get in touch with them. Until you recover the decrypt code from the attacker, you won't be able to use your data that is held.
Why is Ransomware so effective?
The reason for their effectiveness is that they use custom programs that are capable of breaking into systems without login credentials. Since mostly the attackers belong to the countries having less-effective law enforcement, they are free to operate without any regulation.
Is ransomware a virus?
Yes, you can label it as a virus but not exactly a kind of virus.
Can ransomware steal data?
Yes, ransomware attacks can lead to data theft, but only in some cases. Generally, these attacks only encrypt or freeze a system's applications and data and don't expose the data.
How is ransomware installed?
Ransomware can be installed from various sources, beginning with loopholes in the existing security system to the phishing emails. Once they get into the system, they don't only install their software, they also uninstall previous security arrangements.













